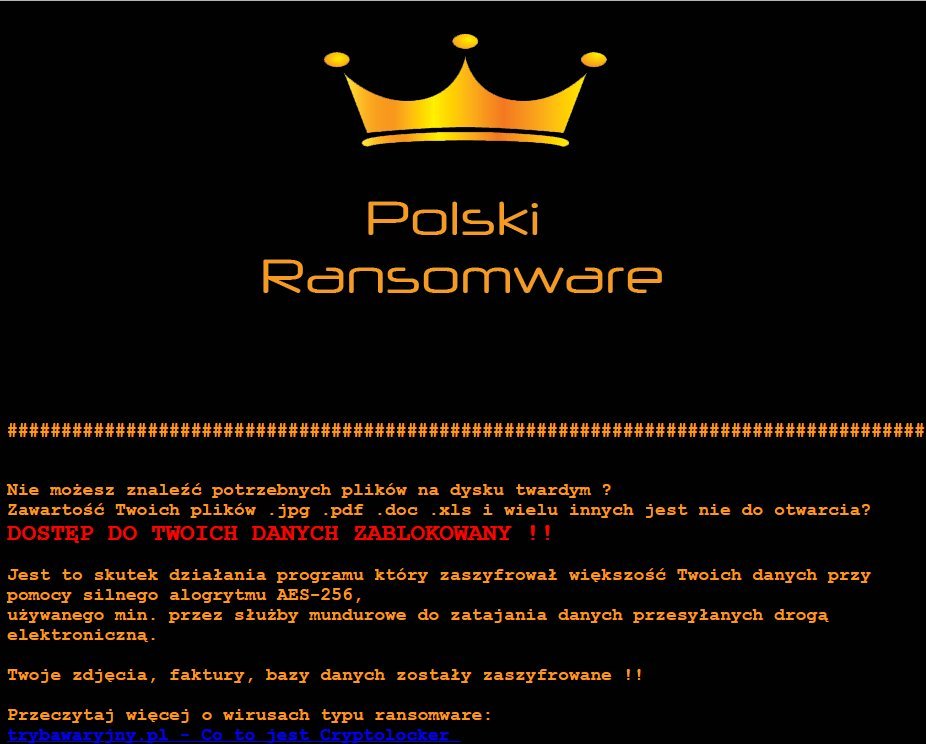
Polish law enforcement announced on Friday the arrest of Tomasz T., a well-known cyber-criminal believed to be the author of the Polski, Vortex, and Flotera ransomware strains.
The arrest took place on Wednesday, March 14, in the Polish town of Opole, while Tomasz —a Polish national living in Belgium— was visiting his native country.
Authorities recovered encryption keys
Polish infosec experts had been tracking Tomasz for years, and Polish police were ready at the time of his arrest. Working through Europol, Polish police alerted their Belgium counterparts, who searched his house and seized computer equipment.
Authorities were able to recover data from the suspect’s laptop and remote servers, including encryption keys. Polish police are now encouraging victims of the Polski, Vortex, and Flotera ransomware families to file official complaints with local authorities so they can receive a decryption key for their files.
The suspect was taken into custody, charged with 181 different crimes, and a judge approved a period of temporary detention of three months. The District Prosecutor’s Office in Warsaw said the suspect pleaded guilty and cooperated with investigators.
Tomasz “Armaged0n” T. was active since 2013
An assortment of people have been tracking this prodigious cybercriminal. According to prosecutors, the suspect has been active since 2013, when he first started targeting users via a banking trojan that would replace bank account numbers in users’ clipboards with one of his own, so to receive undeserved bank transfers.
Since the start of 2017, police say Tomasz shifted operations to ransomware. He first created the Polski ransomware in late January, moved on to the Vortex strain in March, and then to the Flotera strain later in the same month.
Of the three, the Vortex strain remained active through 2017 and 2018. The vast majority of victims were located in Poland, according to data Bleeping Computer received from the ID-Ransomware service.
Online, Tomasz operated under the nickname “Armaged0n,” which he used on the infamous HackForums cybercrime portal.
Polish tech news site Zaufana Trzecia Strona (ZTS) was the first to draw the lines between the three ransomware strains to the Armaged0n persona and later tracked down a large email spear-phishing operation.
To distribute his ransomware, and even other malware strains, Tomasz often sent emails to victims posing as a representative from well-known companies active in Poland, such as DHL, Zara, Cinema City, PAY U, WizzAir, but also local Polish companies and state agencies.
Crook made over $145,000 (117,919.80 Euro)
ZTS, CERT Poland, security researchers, police, and the impersonated companies all collaborated to track down the suspect. Police say they suspect Tomasz infected thousands of users with ransomware and made over $145,000 ( 117,919.80 Euro) from his criminal endeavors.
According to prosecutors, law enforcement was able to track down the suspect through ransomware payments.
Tomasz would gather the ransomware payments in Bitcoin, transfer the funds to a central account, and then exchange the funds in fiat currency at a Polish cryptocurrency exchange via an account associated with his name. Once investigators tracked down his real-world persona, they only had to lie in waiting.
Even before Polish authorities arrested Tomasz, US security researcher Michael Gillespie had created a decrypter for the Vortex ransomware that he was offering to victims in private. Speaking to Bleeping Computer, Gillespie said he’d reach out to CERT Poland to offer the decrypter so the organization could help victims with a ready-made decryption utility. Gillespie is set to receive an honorary award from the FBI later in April for his work on helping ransomware victims.