Microsoft has released multiple microcode updates that mitigate additional variants of the speculative code execution vulnerabilities affecting Intel processors. The patches cover the recently disclosed CPU flaws generically referred to as Foreshadow or L1 Terminal Fault.
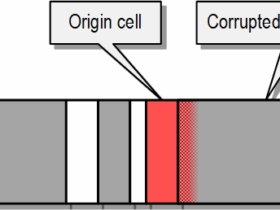
All security gaps covered by these patches are varieties of the Spectre vulnerability revealed on the first days of the year. It affects all microprocessors that use branch prediction and speculative code execution to increase performance. In plain terms, the CPU tries to guess the destination of the code and runs it in memory.
Additionally, they can help get data that is regularly protected from virtual machines running on a host OS’ Virtual Machine Monitor (VMM).
Patches cover all Window 10 versions
The CPU maker finished validating the microcode revisions and delivered them to industry partners further down the chain to ensure protection against security exploits targeting its processors.
As a result, there are now four new updates available from Microsoft (KB4346084, KB4346086, KB4346087 and KB4346088) that apply mainly to Windows 10 versions: Creators Update, Anniversary Update, April 2018 Update and RTM.
Two of them, KB4346087 and KB4346084, are also intended for Windows Server 2016 and Windows Server Version 1803 (Server Core).
With these patches, Microsoft covers Spectre variant 3a (CVE-2018-3640 a.k.a. Rogue System Register Read), and variant 4 (CVE-2018-3639 a.k.a. Speculative Store Bypass); and L1 Terminal Fault (CVE-2018-3615, CVE-2018-3620, CVE-2018-3646).
Before installing the microcode patches users are advised to make sure that the system benefits from mitigation against Spectre Variant 2.
All these updates come with the warning to check the websites for Intel and your device manufacturer for recommendations before installing the microcode from Microsoft.
Although none of them have known issues, it is possible that certain hardware configurations require additional steps to fully solve the problem.