BREAKING —MikroTik has released firmware patches for RouterOS, the operating system that ships with some of its routers. The patches fix a zero-day vulnerability exploited in the wild.
A MikroTik engineer said yesterday that “the vulnerability allowed a special tool to connect to the [MikroTik] Winbox port, and request the system user database file.”
The attacker would then decrypt user details found in the database, and log into the MikroTik router.
Zero-day spotted on Czech forum
According to the users of a Czech technology forum, who first spotted the attacks, the hacks followed a similar pattern. The attacker would have two failed Winbox login attempts, a successful login, would change a few services, log out, and then come back a few hours later.
All attacks were carried out by targeting Winbox, a remote management service that MikroTik provides with its routers to allow users to configure devices from across a network or the Internet. The Winbox service (port 8291) ships enabled by default with all MikroTik devices.
Zero-day was not mass-exploited
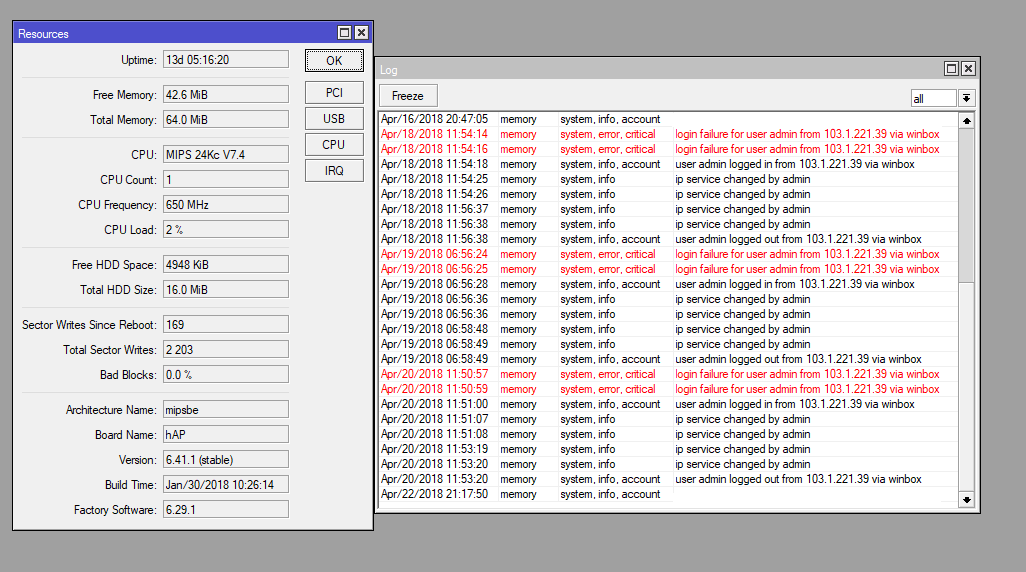
The good news is that all attacks were carried out from one IP address only, suggesting this was the work of a lone hacker. The IP address that all users reported seeing attacks coming from was 103.1.221.39, assigned to Taiwan.
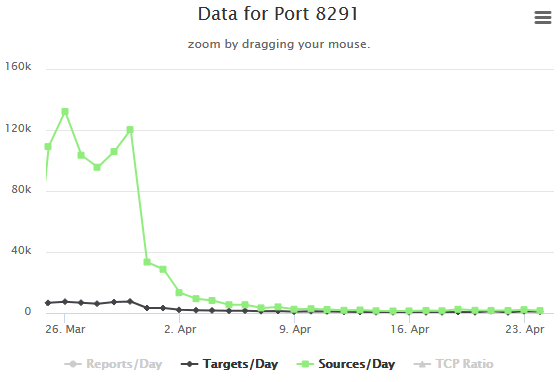
The MikroTik zero-day exploitation attempts were on a very small scale, hardly registering on port activity trackers, such as the ones provided by SANS ISC and Qihoo 360 Netlab.
MikroTik says the zero-day vulnerability affected all RouterOS versions released since v6.29. The company patched the zero-day in RouterOS v6.42.1 and v6.43rc4, released earlier today.
The company took less than a day from user reports to putting out a patch. Judging that some vendors take months and years to release firmware patches, MikroTik’s response time is quite impressive.
Users advised to change passwords, Winbox port
Since the attacker stole the user database file and there’s no way of telling what routers have been compromised in these attacks, MikroTik engineers recommend that all device owners change their router’s admin account passwords.
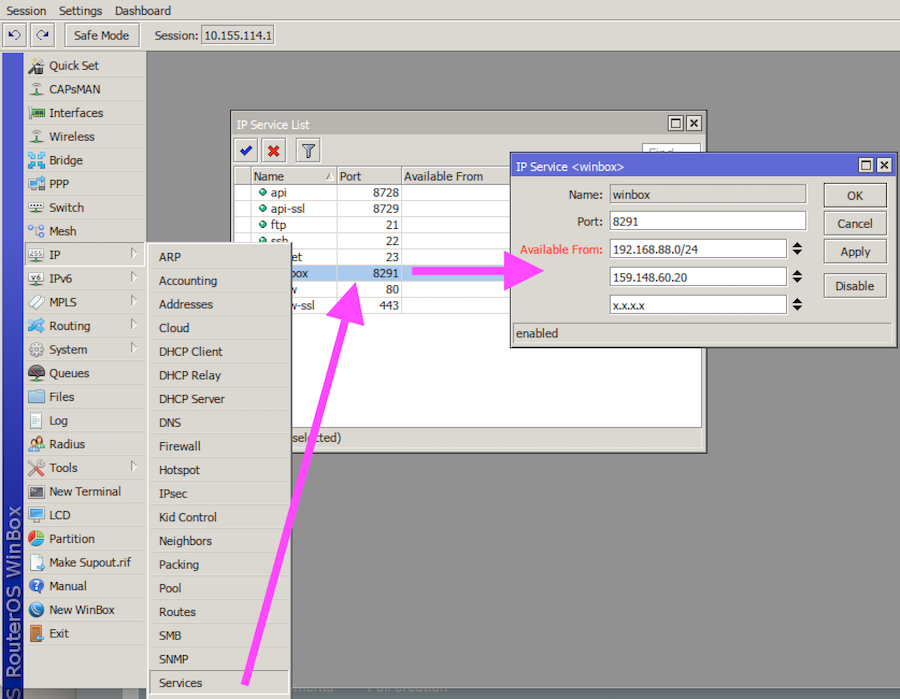
Besides updating the router’s firmware, MikroTik engineers also advise users to use the Winbox utility itself to either change the Winbox port to another value or use the “Available From” fields to limit the port’s availability to selected IPs and IP ranges. See image below for guidance.
This zero-day (which doesn’t have a CVE identifier yet) should not be confused with a recent vulnerability discovered by CORE Security researchers (which affects the router’s SMB service), and is not the same vulnerability recently exploited by the Hajime botnet.
UPDATE [April 25]: Kaspersky Lab security researcher Costin Raiu has identified the payload dropped by the attacker accessing MikroTik routers. According to Raiu, the attacker drops a Lua-based malware on infected routers.
New MikroTik zero day attack patched yesterday installs mips malware that appears related to Luabot, fetches next stage from two hardcoded C2s. pic.twitter.com/Kvyy4QYKVd
— Costin Raiu (@craiu) 25 April 2018
According to Qihoo 360 Netlab, the malware is related to the IoT Reaper botnet.
My team has been tracking this botnet for a while, although it looks like Luabot, it is actually from a branch of the updated IoT Reaper family, which happens to add Lua support, and there are a few more other C2s. We have blocked related C2s since 04/16 https://t.co/oz4ExCYZ3n
— yiminggong (@yiminggong) 25 April 2018